By Paul Colwell, Chief Technical Officer, CyberGuard Technologies
In tackling the question of ‘How can solicitors maintain security?’ I did a Google search and found an interesting article by one of our partners, Carbon Black, talking about the criminal equation. Why do criminals carry out crimes? In reality it’s a simple cost benefit equation.
The Criminal Equation
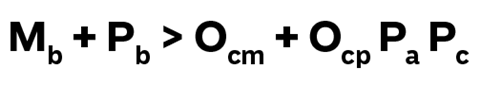
For those without a degree in mathematics, let me explain:
- Mb + Pb - what do I stand to gain from committing the crime… monetary or psychological benefits?
- Ocm + Ocp - what do I stand to lose if I get caught? My freedom, and how much time do I have to invest?
- Pa Pc - what are the chances that I will get caught and convicted?
Discouraging cybercriminals
We all know there is little or no chance of a conviction when dealing with cybercrime. If there is a slim chance of getting caught, what discourages cybercriminals from hacking your network?
Nothing, and this completely changes the results of the equation in today’s digital world.
The only reason a network hasn’t been compromised is that it hasn’t been worth the cybercriminal’s time.
As sobering as the equation is, it makes one thing clear. We simply need to make this cost benefits equation equal out! We don’t need to make it impossible to break into, we only need to make the cost of breaking in greater than the value of our data.

So we start by understanding our data; not only the value of it, but also where it is and who has access to it.
Once we understand that, we can formulate a plan. Unfortunately there’s no magic fairy dust, and no one product that can make all your information security problems disappear. You need a layered approach and it’s not just IT’s responsibility, it needs complete buy-in from the business, the partners and users, to make it work.
This approach has always been the best advice and remains true of information security today.
We work on four pillars of security
Firstly, Testing. Before you do anything you need to understand your starting position. To do this it’s best to employ an independent third party security company, that doesn’t currently look after your IT infrastructure, to critically assess your network. We use the same tools as hackers to identify critical weaknesses in customers’ defences. These services normally include Penetration or Vulnerability Testing, or Security Gap Analysis. This creates the baseline for your infrastructure and it allows you to quickly remediate and close any gaps.
Secondly, Detect and Respond. Nearly every company I go to has already deployed security products whether that’s a firewall at the perimeter of the network, or anti-virus on the users’ machines. Relying on these products alone is not enough to protect you as cybercriminals can easily circumvent these solutions, neither is adding more products. What is important, is that these products are monitored and alerts or indicators of compromise are investigated before they are allowed to take hold and spread through the network. Enterprise companies employ teams of security professionals but most medium and small businesses can’t afford this and responsibility falls to the IT Manager. Even the best IT Managers I speak to don’t have time in between their heavy workloads to investigate the millions of logs generated by the firewall. Outsourcing your security to experts is usually the best and most cost effective solution.
The third pillar concentrates on the human layer - Staff Awareness. Most modern day attacks start with some user interaction and are successful because someone clicked on a link, installed some software, opened a suspicious email or visited a malicious website. Users can, and should, be trained in the basics of information security to enable them to identify suspicious emails, set strong passwords and handle sensitive data appropriately.
Finally, Certification. I encourage all customers to meet the standards set out by the government in the Cyber Essentials scheme. This is a great starting place to test your security, not only ensuring you have the basics right but also demonstrating to your customers and business partners that you take data security seriously. To further enhance your security you can look at other schemes such as Cyber Essentials Plus, IASME Gold and ISO 27001.
In the ever-changing world of cyber security, maintaining security can be challenging but getting the basics right will go a long way to protecting you and your business.

Worcester Road, Stourport‑on‑Severn, Worcestershire DY13 9AT
Telephone: 01299 873 805
Email: security@cg-tech.co.uk
Web: www.cg-tech.co.uk
Twitter: @cg_techuk


























No comments yet